hello i’m
NOUROUDINE MOHAMED
Cyber Security Expert
It's strange is photographer spend year, even entire lifetime, trying to capture moments that together don't even add up to a couple of hours. Life is like a camera .
Get Started

7+
years experience
know me more
I'm Working On A Variety Of Technologies Right Now, Including Cybersecurity, GRC, PCI DSS, Penetration Testing, Cryptography Web 3.0 and Blockchain Technology, .
Governance, Risk, and Compliance (GRC)
In-depth knowledge of GRC frameworks and best practices to ensure organizational compliance and risk management. Skilled in conducting risk assessments and implementing mitigation strategies.
IT Management and Audit
Proficient in IT management and auditing, ensuring optimal performance and security of IT systems. Skilled in developing and implementing IT policies and procedures.
Microsoft Azure Solutions & Security
Expertise in securing Azure environments, leveraging Azure security services to protect cloud-based infrastructures and data.
which service I provide
I Work Creatively And Specially For My Clients You Can Check. Make Your Dream Come True & Grow With Me. I Provide Innovative Solutions For Your Security.
Governance, Risk, and Compliance (GRC)
Risk Assessment and Management
- Conduct comprehensive risk assessments to identify and evaluate risks.
- Develop risk management frameworks and strategies.
- Develop and implement cybersecurity policies and procedures.
- Training and Awareness Programs
Penetration Testing
- Network and Infrastructure Penetration Testing - Application Penetration Testing - Social Engineering and Phishing Simulations - Code review
PCI DSS & ISO & NIST
- Perform gap analysis to identify areas of non compliance - Assist in implementing the necessary controls and processes to meet compliance requirements - Conduct readiness assessments to prepare for formal audits - Provide support during audits conducted by QSAs
Microsoft Azure Solutions & Security
- Configure and optimize security settings in Azure environments. - Implement Azure Security Center and other native security tools. - Perform security assessments of Azure cloud environments. - Implement and manage Azure Active Directory (AD)
Managed Security Service Provider (MSSP)
- Configure security information and event management (SIEM) systems - Configure security information and event management (SIEM) systems and other MSSP tools. - Design and implement Security Operations Centers (SOCs). - Conduct proactive threat hunting to identify and mitigate advanced threats. - Design secure IT architectures that align with business objectives. - Implement data protection strategies and technologies. - Develop and test business continuity and disaster recovery plans.
150+
Happy Customer
36+
Project Done
98%
Uptime Server
168+
network sensor
why choose me
I Have Been Working In Cyber Security For Companies Around The World For More Than 07 Years. Learns Everything There, From It is Medieval Roots To The Modern Age.
Provide Advanced Security for Advanced Threat
Multiple Layers Of Security Are Dispersed Across The Computers, Networks, Programs, Or Data That One Wants To Keep Secure.
Certified and Professional Expert
For Business To Have A Successful Defense Against Cyber attacks, The People, Processes, And Technology.
Security on a global scale
By Automating Interconnections Across A Few Cisco Security Products
24/7 Premium Support
Unified Threat Management System May Speed Up Crucial Security Operations Tasks Like Detection.


privacy is a human right and it belongs to you
Your Website, Web Servers, And Web Apps Are Protected By The Complete And Tested Solution Suites Offered By STEGNOS, The World Leader In Automotive Cyber Security. Shield Leverages
Get StartedIssues with recent fixes
I'm Working On A Variety Of Technologies , Including Technology, Cybersecurity, Cryptography Web 3.0, And Blockchain.
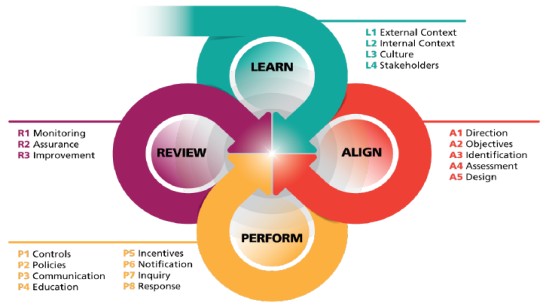
Governance, Risk and Compliance
Adopt an efficient management system owing to our consultants skills in various areas:
- Implementation of a Business Continuity Management System (BCMS) in accordance with ISO 22301, and an Information Security Management System (ISMS) in accordance with ISO 27001.
- Development of cybersecurity master plans
- Setup of a cybersecurity policy
- Data classification

Penetration Testing
Analyze The Current Security Posture
- Network and Infrastructure Penetration Testing
- Social Engineering and Phishing Simulations
- Application Penetration Testing
- Code review

PCI DSS
Payment Card Industry Data Security Standard
Analyze The Current Security Posture
- PCI DSS Gap Analysis
- PCI DSS Compliance Implementation
- Quarterly and Annual Audits

MSSP
Managed Security Service Provider Solutions Deployment
- Deploy and manage MSSP solutions to provide continuous monitoring and threat detection.
- Configure security information and event management (SIEM) systems and other MSSP tools.
- Design and implement Security Operations Centers (SOCs).
- Provide SOC staffing, training, and operational support.
companies I have work with
I'm An Cyber Security Specialist With Experience In A Variety Of Related Fields Including Governance Risk and Compliance(GRC),IT Audit and Risk analysis,PCI DSS, Penetration Testing, Network Security, Vulnerability Management, Intrusion Detection., Vulnerability Management, Intrusion Detection.
my achievements
Advanced Threat Protection. I've Been In The It Industry Since 2006, And In 2009 I Began To Concentrate On It Security. Since Then, I Have Worked
Cannes Lions 2022 Poster Design
Managed Cybersecurity Operations That Protect Your Business. I Provding All Type Of Cyber Security Services And Solutions.
OneShow 2021 New York Poster Series
Protect Your Website, Server, Service, And Application Against The Increasing Sophistication Of Hacker Threats. Start Protecting Your Data Today.
AGDA Awards 2020 Design Crafts
Make Your Dream Come True & Grow With Me. I Provide Innovative Solutions For Your Security. Secure Your Data And Assets As Soon As Possible.
D&AD 2021 Typography for Advertising
Multiple Layer Security Dispersed Across The Computers, Networks, Programs, Or Data That One Wants To Keep Secure In An Cyber Security.
Get in touch
I'm An Cyber Security Specialist With Experience In A Variety Of Related Fields Including GRC,IT Audit and Risk analysis,PCI DSS, Penetration Testing, Network Security, Vulnerability Management, Intrusion Detection..